
Secure and Frictionless Authentication
With No Algorithm To Crack

Zero Knowledge Password Proof
Secure account log in without ever revealing your PIN

Highest Security At Scale
Based on One-Time Pad Principles

No Algorithm To Crack
Piece of mind knowing your credentials can never be compromised
Do you need Secure and Frictionless Authentication?Watch this 30 second demo to see Secure SMS by TokenOne in action

How are we different from other authentication systems?
With TokenOne you never enter your PIN.Unlike other solutions that rely on the user entering their 'secret' password to prove they know it. TokenOne uses a combination of smart device identification and Zero Knowledge Password Proof. So users can authenticate without revealing their secret TokenOne PIN.
About TokenOne
Highest Security At Scale
TokenOne is a cyber security software company based in Sydney focused on the prevention of identity theft.Based on tried and tested principles of One-Time Pad from the Cold War and before, TokenOne’s patented technology provides the strongest form of authentication security but is also extremely simple.So, unlike any other authentication security technology, TokenOne achieves both highest security AND highest scalability.
How Is TokenOne Different From Other Authentication Systems?
The key differentiator to other authentication services is that TokenOne proves user presence. We provide genuine strong Two-Factor Authentication, as both factors are strong. There are three accepted factors in Authentication:Something you know – the knowledge factorSomething you have – the possession factorSomething you are – the inherence factorWith TokenOne you never reveal your secret PIN – so the knowledge factor remains strong. Unlike other solutions that rely on the user entering a ‘secret’ (usually a password) to prove they know it, TokenOne changes the knowledge factor paradigm by enabling proof of the knowledge factor without ever revealing it. This makes the TokenOne PIN a ‘zero knowledge password proof’ and sets a new standard for Authentication.The second factor, the possession factor, is your smart device. This has been profiled and must also be present to prove you are an authorised user.With TokenOne Authentication both factors are strong. TokenOne allows organisations to prove who is accessing your site or service. This is vital not only for the security of sensitive information but also for compliance.
Authentication Comparison

How It Works
TokenOne allows users to verify their real world credentials and identity, register their phone as a token and create a secure and secret PIN. A user can complete all necessary steps in a way that enables an organisation to meet both identity proofing and legal compliance requirements. Users can also add credentials as required by an organisation’s business rules.
Deployment of TokenOne Authentication
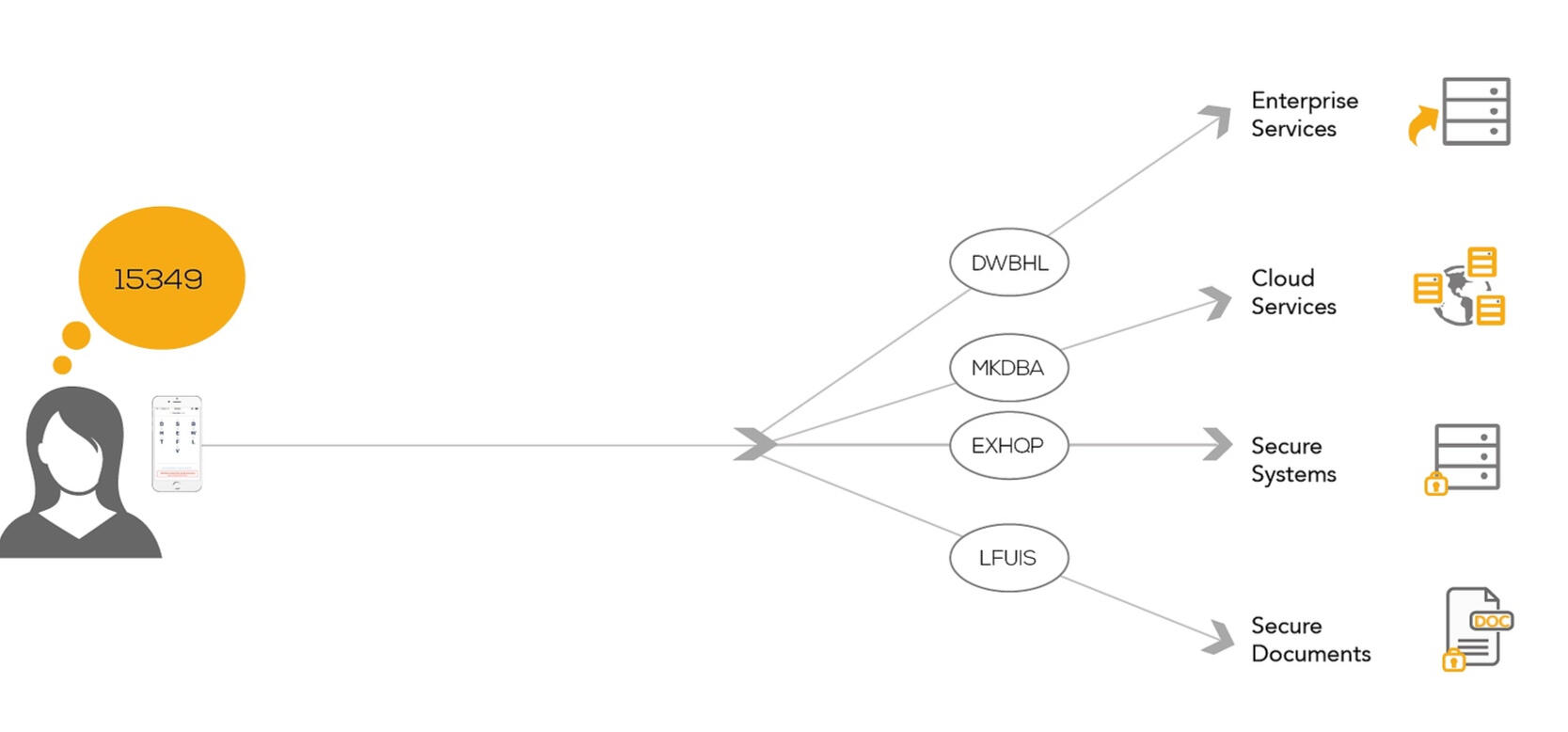
The Problem
With cybercrime now costing more than US$445 billion globally per year, organisations are facing increasing challenges to continually improve security and prevent unauthorised access to high risk or sensitive information and services.Deal rooms, client portals, corporate records and critical systems often only require a username and password. Where Two-Factor authentication is provided, it is often cumbersome, expensive to manage and difficult to deploy.At the same time, users are demanding security of their identity, their information and dealings with all service providers and expect a convenient, secure and easy-to-use service too. As a result, organisations have to balance consumer demands while meeting their security and compliance requirements.
Patented Technology
Based on principles of industry recognised uncrackable form of encryption (One-Time Pad).
Authentication
Secure and simple by proving the presence of the device and mentally scrambling the PIN.
Self Management
Users register their device as a true and unique token and create their own PIN. Ongoing management of both is also done by the user.
No Algorithms
Ensures TokenOne is not vulnerable to someone cracking an algorithm and compromising multiple accounts and all the reliant services and infrastructure.
Genuine strong 2FA
As both factors are strong, TokenOne proves the presence of the device AND the user and is one of the few mass market authentication solutions where both factors are strong.
PIN never revealed
The user knows their PIN which is never entered or revealed to anyone, not even to TokenOne or the service the user is accessing.
Contact Us
© 2023 TokenOne. All rights reserved.Registered trademark in Australia & the United States.